By clicking on the green eye button placed at the end of each result, you can access the message detail page. The message detail page has a general email data section and 5 additional sections containing advanced information. All the sections will be explored in depth below.
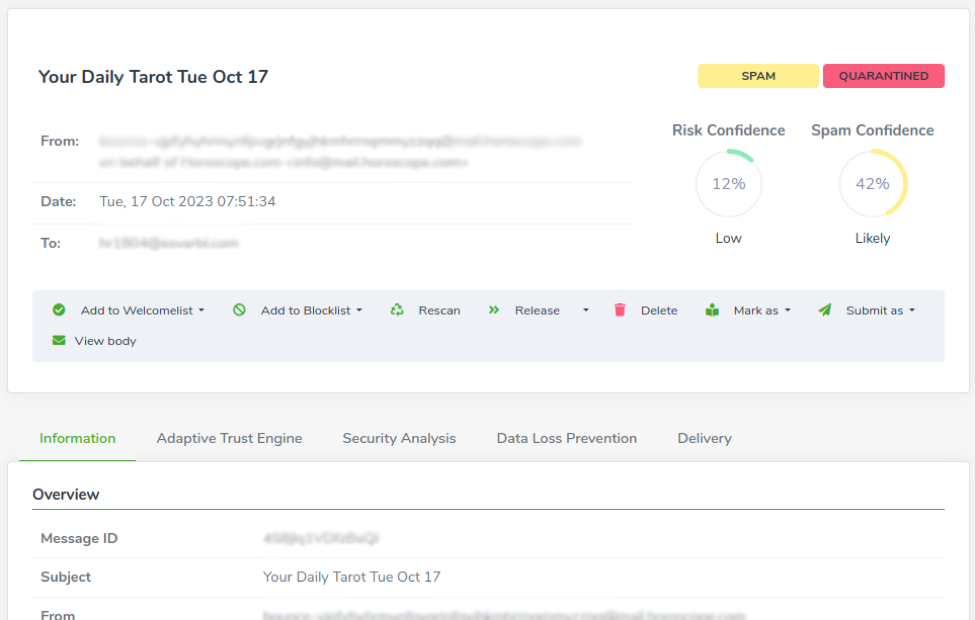
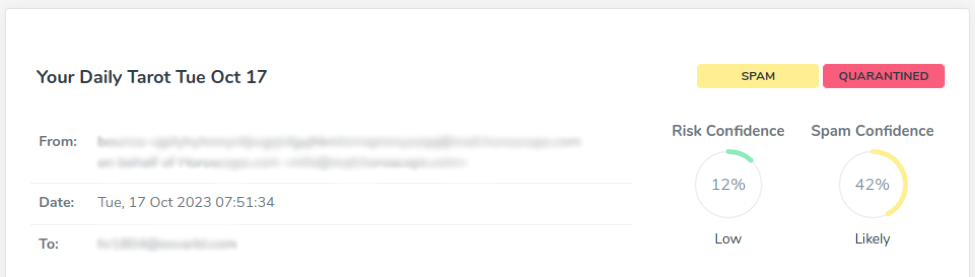
In the first section displays basic information about the message, and the message badges are located in the top right corner.
The first badge represents the SEARCH RESULTS EXPLAINED, the second one represents the last action the Email Security performed on the message (quarantined, delivered, deferred etc…).
- Subject (as section title)
- From (the email address where the email is from)
- Date (the date when the email landed on the service)
- To (the email address where the email should be delivered)
- Risk Confidence (a security estimation such as phishing, malware, business compromise emails etc…)
- Spam Confidence (a junk estimation such as spam, newsletter emails etc…)
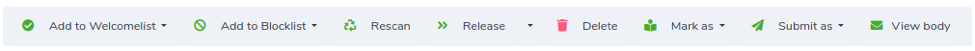
 You can perform many operations for the message you are analyzing:
You can perform many operations for the message you are analyzing:
- Add to Welcomelist (you can choose between the sender IP address or the sender email address)
- Add to Blocklist (you can choose between the sender IP address or the sender email address)
- Rescan (put the message in the scanning queue of the service aiming to get a different scanning result, in case where there are changes to the service settings)
- Release (or Release to (specified address(es)) by clicking on the arrow to the right on the button
- Delete (completely remove the message from the service)
- Mark as (this message will be learned by the bayesian engine as good or bad)
- Submit as (submit the message, as good in case of false positive or bad in case of false negative, to us for further analysis)
- View Body (view the email body directly from the EDS interface)
INFORMATION
In this tab, we display both general and detailed information about the message.
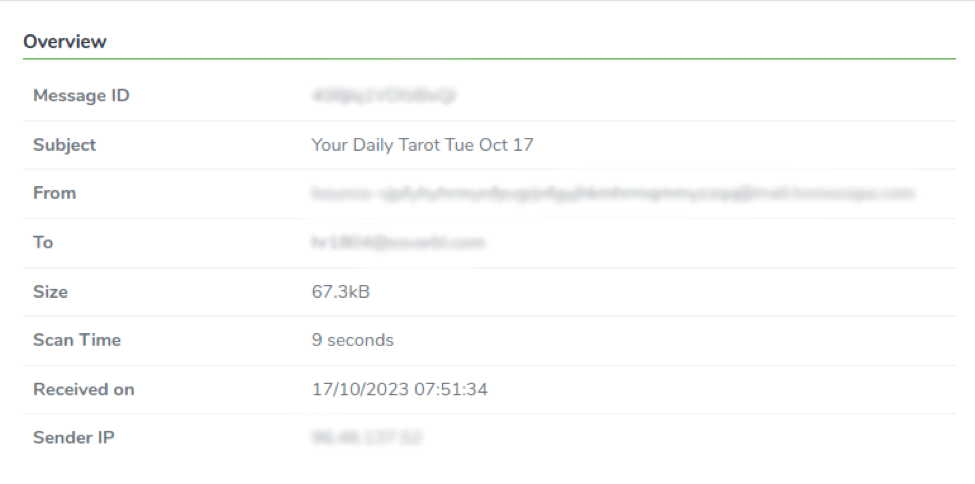
Overview
In the first section of the information tab, we show an overview of the message. We also include less general email information such as the Message ID, the Email Size, the Scan Time, and the Sender IP address.
Authentication
In the second section are shown the authentication results of the message. In this section, we display the results of the SPF, DKIM, and DMARC checks.

URIs
In the third section, we display the URIs contained in the email body.
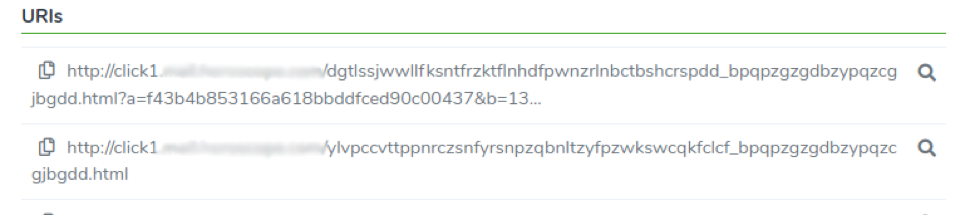
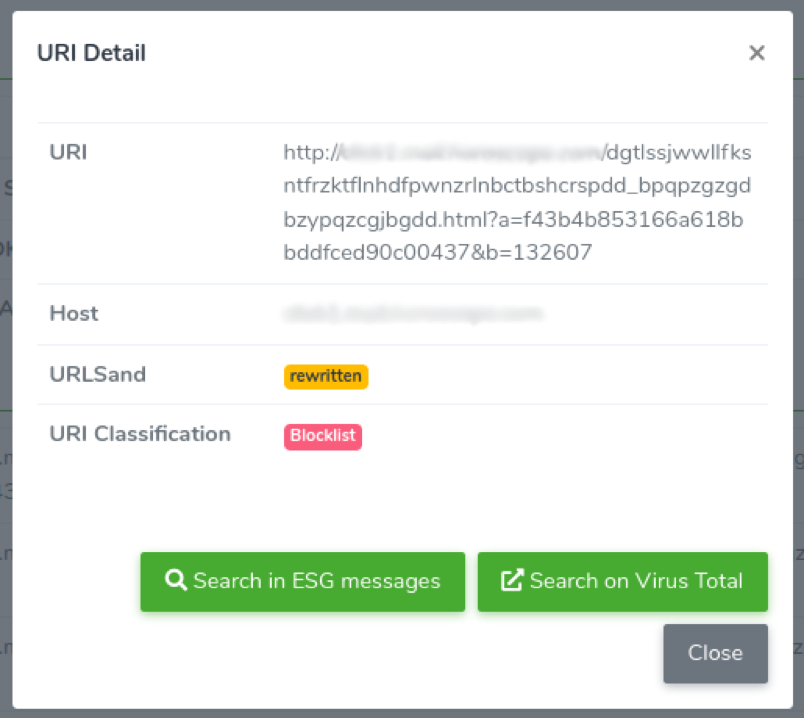
By clicking on the magnifier icon at the end of each URI you can see the URI details and what action the URLS and engine performed. You are also able to search it in all the other messages on the service, or search it on VIRUS TOTAL.
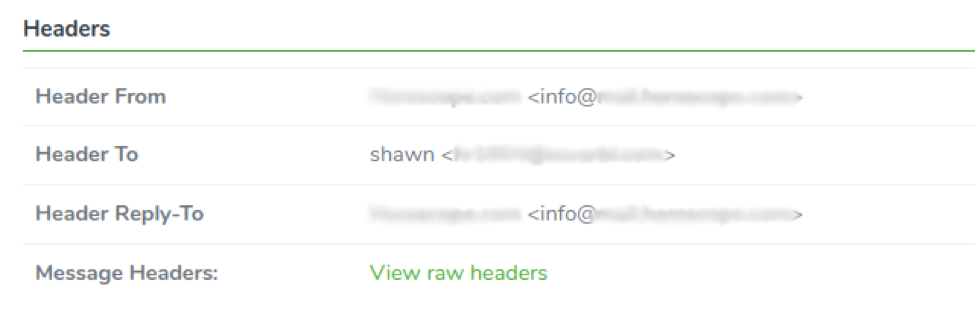
Headers
In the fourth section of the tab, we display the email headers. You can analyze them better by displaying them in a raw format by clicking on the View raw headers link.
ADAPTIVE TRUST ENGINE
In this section, we display all information provided by the Adaptive Trust Engine (ATE) about the message.
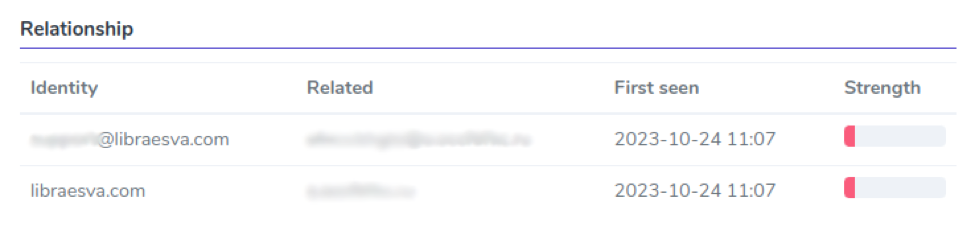
Relationship
In the first section, we display the Adaptive Trust Engine relationship data between all the email addresses involved in the email.
The most important data point is the Strength indicator. This bar indicates the amount of traffic between the sender and recipient. Generally speaking, a phishing or malicious email is less likely to be sent through a bi-directional communication between two people who have a history.
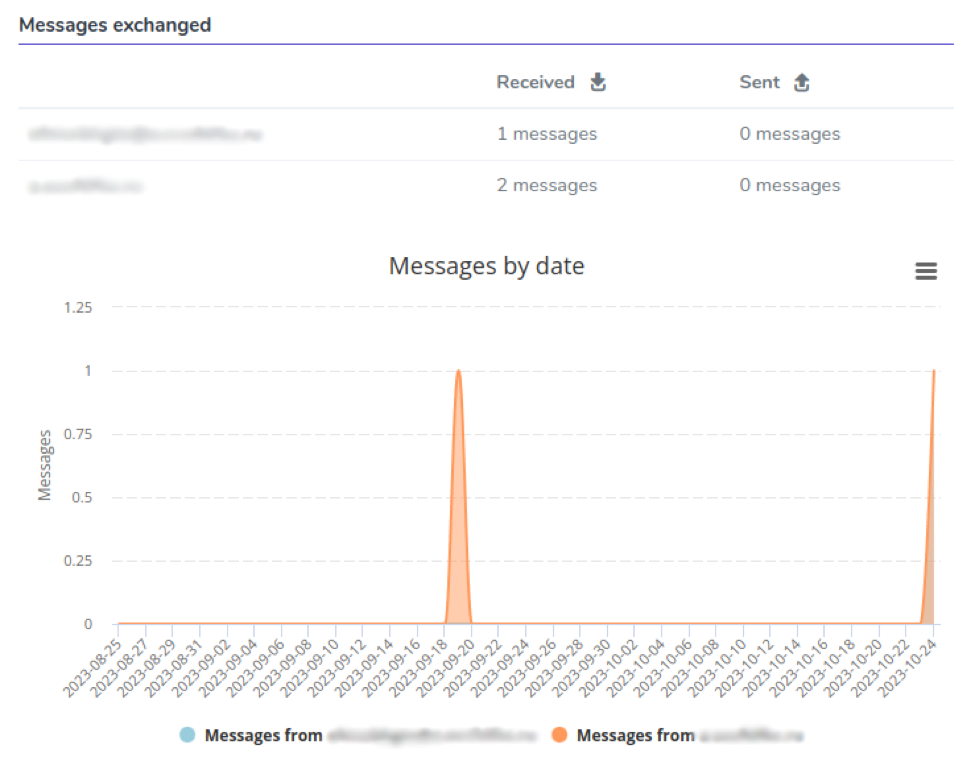
Messages Exchanged
In the second section is shown a chart representing how many messages landed on the service from this email address and domain.
SECURITY ANALYSIS
Here we display the scan results and any action taken by EDS to keep your inbox safe.
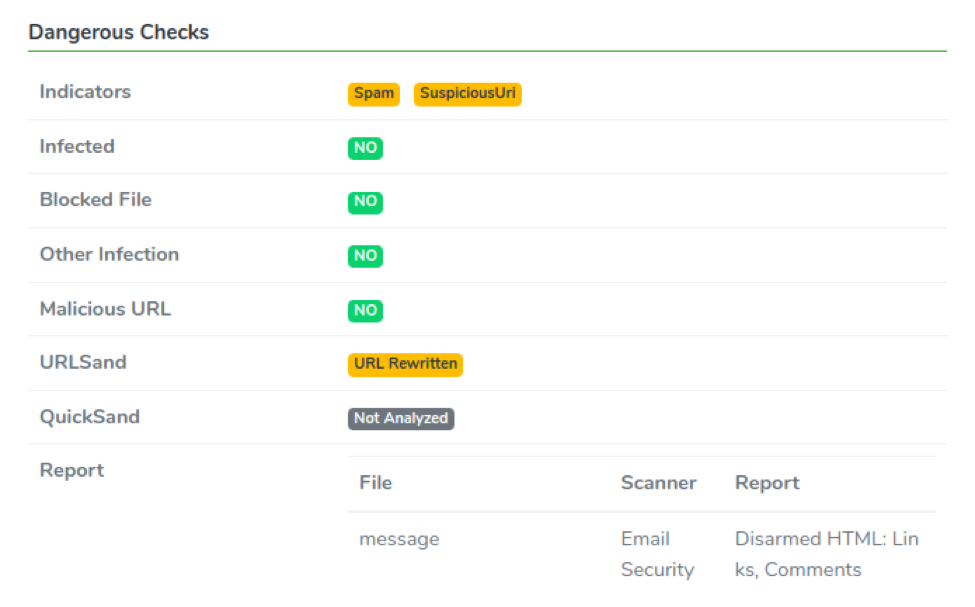
Dangerous Checks
In this section, we display all the scan results and any action taken to sanitize potentially dangerous content like URLs, attachments, hidden code etc…
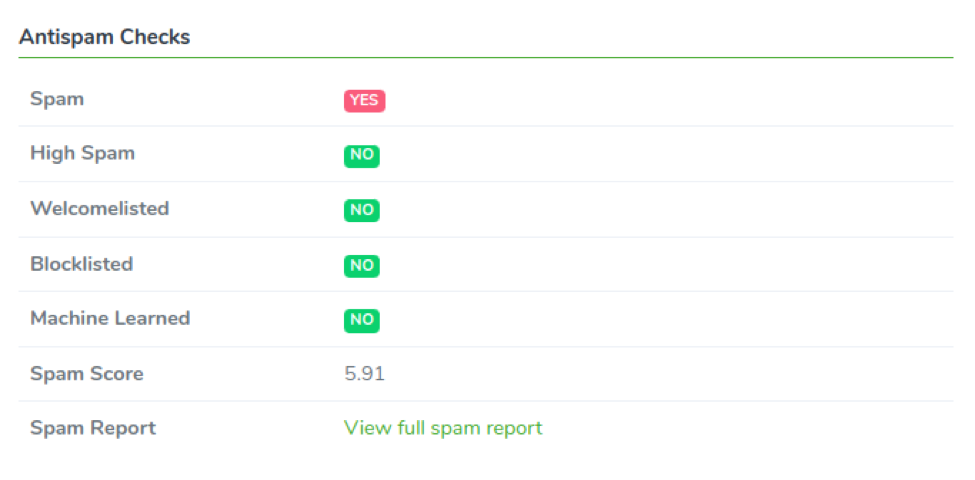
Antispam Checks
In this section, we display all antispam scan results and any block/welcome list interventions. The most important value is the Spam Score. This score is the sum of all scores of the triggered rules shown by clicking the View full spam report link.
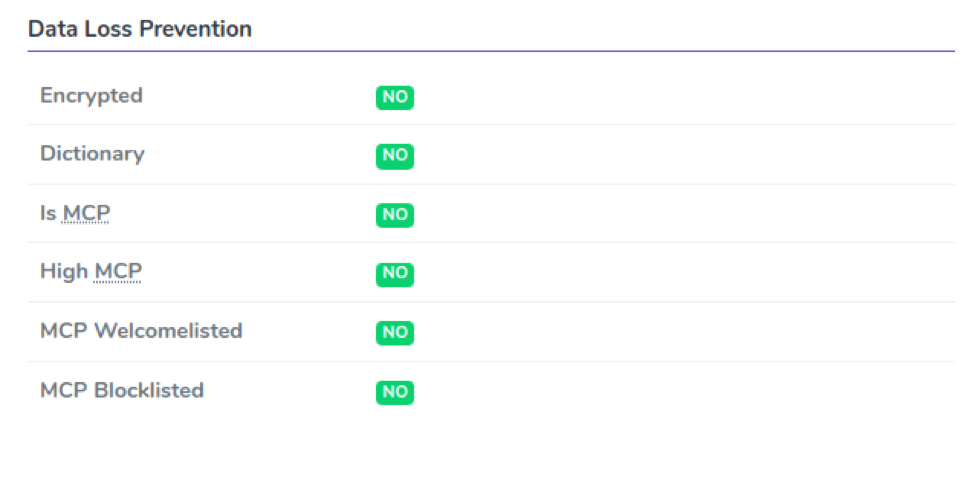
DATA LOSS PREVENTION
In this section we display Data Loss Prevention rules, and whether any have been triggered. These rules prevent critical data sharing if not authorized.
DELIVERY
In this tab, we display all of the delivery information for the message.
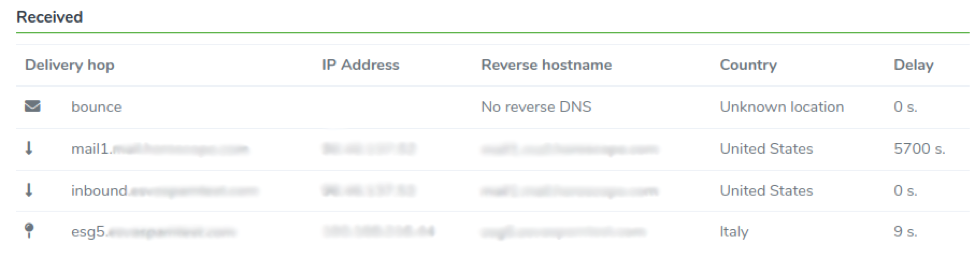
Received
In the upper section of the delivery tab, we display the message delivery trace. This trace is useful to debug delivery issues.
For each hop, we display common information such as the IP address, the Reverse hostname, the Country, and the delivery Delay.
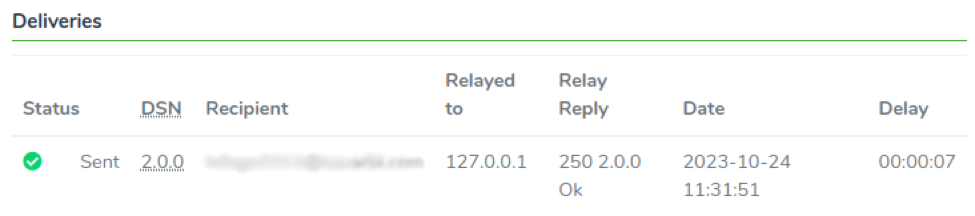
Deliveries
In the second section, we display all the delivery related information such as the DSN, the Relayed to IP address, the Relay Reply, the delivery Date, and the delivery Delay.
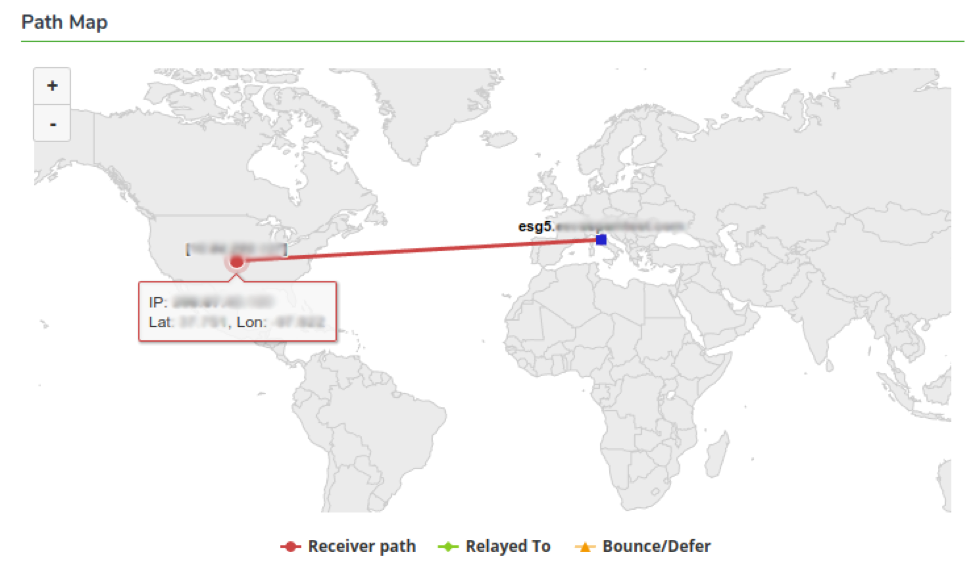
Path Map
In the third section, you’ll find the email trace on a world map to better understand where the email is coming from and where the delivery hops are located.
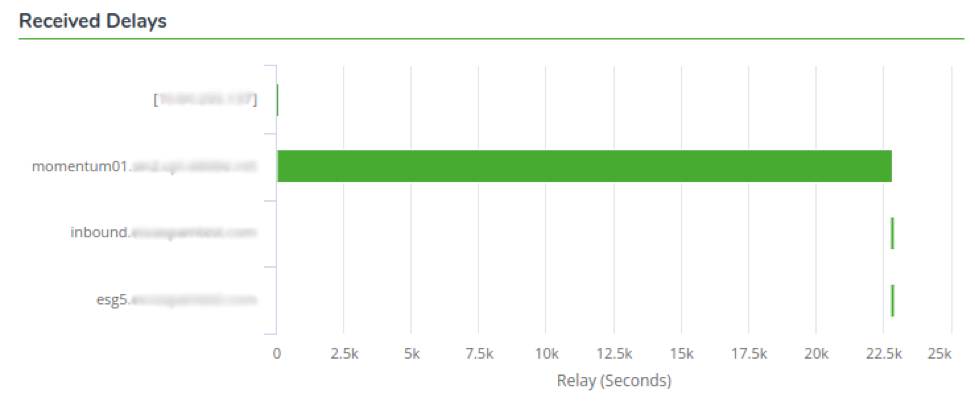
Received Delays
In the last section, we display how many seconds the message waited to leave the hop to reach the next. This tool is useful to drill down to which host is slowing down the delivery process.